This integration will allow you to use GetHub commit comments to update bugs
This will cause any commit comments to be added to bugs references by the comment. E.g. the commit comment “This fixes bug 123” will cause “This fixes bug 123” to be added as a comment to bug 123.
You must configure both Github and devZing to make this work.
Github configuration
To configure GitHub click Settings when viewing your repository
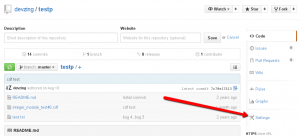
Click Webhooks & Services
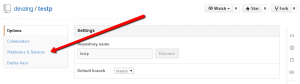
Click Add Webhook
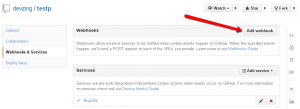
Fill in the Payload URL:
- If using the US datacenter use https://app.devzing.com/<account>/bugzilla/extensions/GithubWebhook/
- If using the UK datacenter https://uk-bz1.devzing.com/<account>/extensions/GithubWebhook/
Content type can be either application/json or application/x-www-form-urlencoded
Feel free to add a secret as we will be supporting this soon.
Make sure you have selected “Just the push event” as other event types will be ignored.
Then click Add Webhook to save your webhook.
devZing configuration
Next log into your devZing account and click “Manage Global Settings”
In the “Github Integration” section select a Bugzilla user that will be used for the integration.
Click Save.
Using
In daily use just include the keyword “bug” next to the Bugzilla defect ID you want to update in the commit message. Remember that the Github webhooks aren’t executed until you push your changes and that there can be several commits in a single push. Every commit message in a push will be evaluated so you can update 1 or 100 bugs in a single push.